Happy New Year! Or so I thought. After a refreshing Christmas vacation with my family, I was stashing something away in our storage room when I noticed the server fan running at maximum speed. This was very unexpected, considering my server is powered by an Intel i3 and should handle all the light tasks I run quite effortlessly. Anyways, I continued unpacking and didn't think much more of it. Today, while running a simulation on my laptop, the fan noise reminded me of my earlier observation. I decided to SSH in to my server to check its status.
To my surprise, when running htop, I saw two processes running at 100% CPU utilization named kdevtmpfsi. Reading the first couple of search results left me baffeled - I had fallen victim for a known malware called Kinsing. It was most likely running crypto-mining activities on full blast on two cores on my server. According to htop, this had been going on for over 8 days.
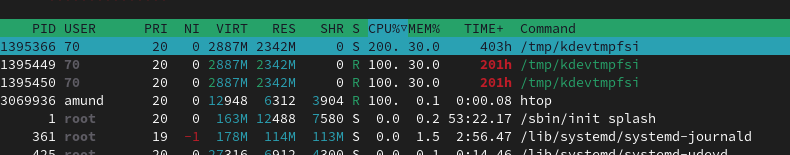
I quickly investigated the potential cause and found that there is an exploit targeting unprotected and exposed Docker containers (source). This was somewhat releiving, as the latest change I made was spinning up a postgres_alpine container in Docker right before the holidays. Spinning it up was done in a hurry, as I wanted to have it available remotely for a personal project while I was away from home. This also meant that it was exposed to the internet, with open ports in the router firewall and everything. Considering the process had been running for 8 days, this means that the infection occured just a day after creating the database. None of the database guides I followed had warned me about the dangers of exposing a docker containerized database to the internet. Ofcourse I password protected it, but seeing as it was meant to be temporary, I didn't dive into securing it properly.
Fortunately, despite the scary log entries showing attempts to change privileges and delete critical folders, it seemed that all the malicious activity was contained within the container. And luckily for me, the kdevtmpfsi processes were terminated when I stopped the postgres_alpine container.
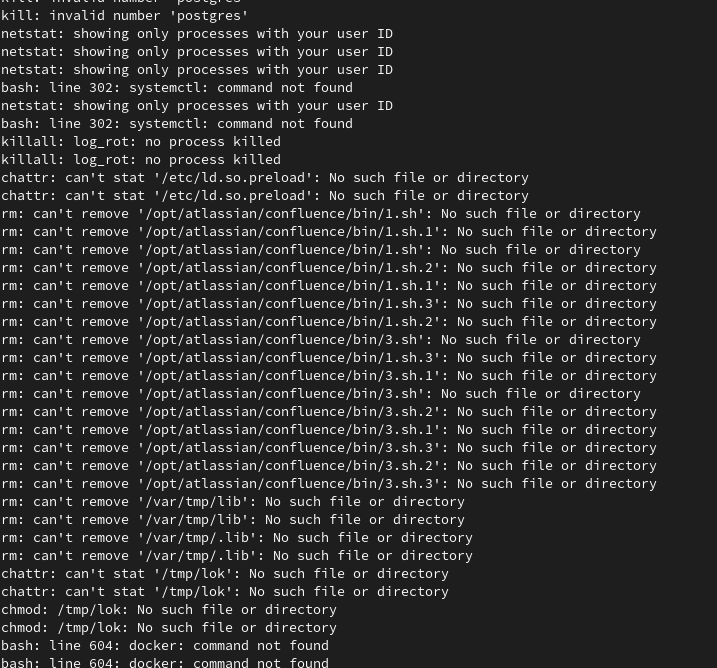
However, while reviewing my system logs, I discovered that someone was constantly trying to brute force their way into my server. A quick IP search revealed that it was registed with a Chinese ISP and located in the Russian Federation. Although I believe it wasn't an immediate threat, I decided to close access to my home network both for VPN and SSH connections to my server. After checking my UPnP and DMZ settings, this results in no ports being open on my home network anymore.
With this, the attack surface of my home network should be limited to exploits against my router firewall, and thus minimized as best as can be. This leaves the problem of me not being able to VPN into my LAN to run simulations on my desktop from the outside, so I might reinvestigate to re-open that at some point. For now, I hope to rest more easily.
For those of you who have not had this seanse yet: Be careful with exposing your home setup to the internet! I have learned my lesson, and next time I want to expose something to the internet, I will make sure to take the necessary precautions.
Happy New Year!